EtherApe
EtherApe is a packet sniffer/network traffic monitoring tool, developed for Unix. EtherApe is free, open source software developed under the GNU General Public License.
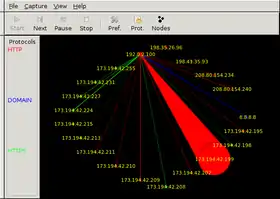 EtherApe GUI | |
| Developer(s) | Riccardo Ghetta, Juan Toledo, Zev Weiss |
|---|---|
| Initial release | February 17, 2000 |
| Stable release | 0.9.19
/ May 15, 2020 |
| Written in | C |
| Operating system | Linux and Unix-like |
| Available in | English |
| Type | Networking |
| License | GNU General Public License |
| Website | https://etherape.sourceforge.io/ |
Functionality
Network traffic is displayed using a graphical interface. Each node represents a specific host. Links represent connections to hosts. Nodes and links are color-coded to represent different protocols forming the various types of traffic on the network. Individual nodes and their connecting links grow and shrink in size with increases and decreases in network traffic.
EtherApe version 0.9.14-1[1] still depends on GConf, GnomeVFS and GTK+ version 2. Sooner or later somebody might port it to dconf, GVfs, D-Bus and GTK+ version 3 or 4.
History
Originally authored by Juan Toledo, the first version of EtherApe (version 0.0.1) was released on February 18, 2000. In a 2006 survey, Insecure.org named EtherApe number 43 on its list of the "Top 100 Network Security Tools".[2]
Features
Some of the features listed about EtherApe include (the following list refers to version 0.9.15 of EtherApe):
- graphical network traffic display
- color-coded node and links for most used protocols
- optional background image
- traffic may be viewed on one's own network, end to end (IP) or port to port (TCP)
- a variety of frame and packet types are supported
- data view can be manipulated using a network filter
- clicking a node or link provides additional information regarding including protocol and traffic information
- summary protocol and node table
- can read traffic from a file or an actual network
- handles traffic on Ethernet, WLAN, VLAN plus several other media and encapsulation types
- supports both IPv4 and IPv6
- XML export of node statistics
- "central node ring" mode.
- "column" mode.
- optional name resolving using c-ares library
- packet capture and display run on different processes
Security
EtherApe requires root privileges to capture packets (but not to replay captured files). As of release 0.9.15 capturing is delegated to a separate process, while the main interface can run with lower privileges, significantly reducing the risk associated with capturing packets from untrusted sources (e.g. Internet).
See also
- tcpdump, a packet analyzer
- Ngrep, a tool that can match regular expressions within the network packet payloads
- netsniff-ng, a free Linux networking toolkit
- Wireshark, a GUI based alternative to tcpdump
- dsniff, a packet sniffer and set of traffic analysis tools