IP address blocking
IP address blocking is a configuration of a network service that blocks requests from hosts with certain IP addresses. IP address blocking is commonly used to protect against brute force attacks and to prevent access by a disruptive address.
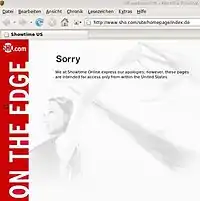
IP address blocking can be used to restrict access to or from a particular geographic area, for example, the syndication of content to a specific region, otherwise known as geo-location and geo-blocking.
How it works
Every device connected to the Internet is assigned a unique IP address, which is needed to enable devices to communicate with each other. With appropriate software on the host website, the IP address of visitors to the site can be logged and can also be used to determine the visitor’s geographical location.[1][2]
Logging the IP address can, for example, monitor if a person has visited the site before, for example to vote more than once, as well as to monitor their viewing pattern, how long since they performed any activity on the site (and set a time out limit), besides other things.
Knowing the visitor’s geo-location indicates, besides other things, the visitor’s country. In some cases requests from or responses to a certain country would be blocked entirely. Geo-blocking has been used, for example, to target Nigerian IP addresses due to the perception that all business originating from the country is fraudulent, thus making it extremely difficult for legitimate businesses based in the country to interact with their counterparts in the rest of the world. To make purchases abroad, Nigerians must rely on proxy servers to disguise the true origin of an Internet request.
Internet users may circumvent geo-blocking and censorship and protect personal identity and location to stay anonymous on the internet using a VPN connection.
On a website, an IP address block can prevent a disruptive address from access, though a warning and/or account block may be used first. Dynamic allocation of IP addresses by ISPs can complicate incoming IP address blocking, rendering it difficult to block a specific user without blocking many IP addresses (blocks of IP address ranges), thereby creating collateral damage.
Implementations
Unix-like operating systems commonly implement IP address blocking using a TCP wrapper, configured by host access control files /etc/hosts.deny and /etc/hosts.allow.
Both companies and schools offering remote user access use Linux programs such as DenyHosts or Fail2ban for protection from unauthorised access while allowing permitted remote access. This is also useful for allowing remote access to computers. It is also used for Internet censorship.
Avoiding address blocking
Proxy servers and other methods can be used to bypass the blocking of traffic from IP addresses.[3] However, anti-proxy strategies are available.
In a 2013 United States court ruling in the case Craigslist v. 3Taps, US federal judge Charles R. Breyer held that circumventing an address block to access a website is a violation of the Computer Fraud and Abuse Act (CFAA) for "unauthorized access", punishable by civil damages.
See also
References
- "What is an IP address?". HowStuffWorks. 2001-01-12. Retrieved 2019-12-13.
- "How cookies track you around the web & how to stop them". Privacy.net. 2018-02-24. Retrieved 2019-12-13.
- "How to: Circumvent Online Censorship". ssd.eff.org. Archived from the original on 2018-12-23.
![]() Media related to IP address blocking at Wikimedia Commons
Media related to IP address blocking at Wikimedia Commons