Stacheldraht
Stacheldraht (German for "barbed wire") is malware which performs a distributed denial-of-service (DDoS) attack. It runs on Linux and Solaris. It detects and automatically enables source address forgery. It was written by "random", of the Austrian hacker group TESO.
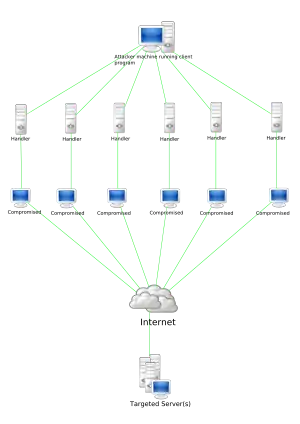 Stacheldraht attack diagram | |
| Original author(s) | "random" |
|---|---|
| Stable release | 4
|
| Written in | C |
| Operating system | Linux, Solaris |
| Size | 36 kb |
| Type | Botnet |
| Website | http://packetstormsecurity.org/distributed/stachel.tgz |
Stacheldraht uses a number of different denial-of-service (DoS) attacks, including ICMP flood, UDP flood, TCP SYN flood, and Smurf attack.
It combines features of Trinoo and of Tribe Flood Network, and adds encryption.
Stacheldraht was later superseded by Blitzkrieg. Blitzkrieg was maintained by "random" and by a loose group of associates.
See also
- Low Orbit Ion Cannon (LOIC) – a stress test tool that has been used for DDoS attacks
- High Orbit Ion Cannon (HOIC) – the replacement for LOIC used in DDoS attacks
- Fork bomb
- Slowloris (computer security)
- ReDoS
External links
This article is issued from Wikipedia. The text is licensed under Creative Commons - Attribution - Sharealike. Additional terms may apply for the media files.