Signal Intelligence Regiment (KONA)
The Signal Intelligence Regiment (German: Kommandeur der Nachrichtenaufklärung, lit. 'Commander of intelligence') (KONA) was the basic element of the field organisation of the German Army (Heer) signals intelligence organization during World War II.[1][2][3] The KONA regiment were mobile communication reconnaissance units which were assigned to an army group and operated close to the front lines within the theatre of operations to intercept and build intelligence, via evaluation services (cryptanalysis) and disseminate the intelligence to senior staff locally and in the OKH/GDNA headquarters in the rear.[4] To quote World War II cryptographic historian, Christos Triantafyllopoulos: "The KONA units did not have the ability to solve complicated Allied cryptosystems. Instead they focused on exploiting low/mid level ciphers and even in this capacity they were assisted by material sent to them by the central cryptanalytic department. This was the German Army High Command's Inspectorate 7/VI"
Sources
The remains of Signal Intelligence Regiment 1 (abbr KONA 1) was a signals regiment that surrendered to American troops near Tausing, located close to and northwest of Liezen, Austria on 9 May 1945. Commanded by the fanatical Nazi[5] Major Ernst Hertzer, the remains of the regiment consisted of around 700 officers, enlisted men and women who were sent to the abbey at Stift Tepl, that was being used as a Prisoner of War enclosure. They had destroyed all their papers en route except those document they considered the most important for reconstruction of their records. The remaining documents were kept in three briefcases plus a single book. On the afternoon of 9 May, with strong rumours of Russians approaching the area, the three briefcases were burned with only the book remaining. The book remained in the unit vehicles after an extensive search and was never found.[6]
Between 23 May and 28 May 1945, over 350 prisoners were screened at a town called Konstantinsbad close to Plzeň in the Czech Republic. All primary personnel were interviewed, with a further 41 chosen for further questioning. Some reports were written at Plzeň but most TICOM documents relating to KONA units were written between 30 May and 2 June at Oberursel near Frankfurt am Main. Further interrogations were undertaken and more specific information given when the group was moved to Revin.[7] In total, the material created consisted of 31 reports supported with supplements giving information of the makeup and organization of Kommandeur der Nachrichtenaufklärung unit 1.[8]
History

KONA 1 operated in the southern sector of the Russian Front from June 1941 until May 1945, intercepting and evaluating Russian Army, Russian Army Air and the People's Commissariat for Internal Affairs (NKVD) traffic.[9] Certain personnel within Kona 1 appeared to have succeeded in reconstructing the detailed Order of Battle of the Russian military, and in predicting the timing and location of Russian offensive before they occurred[10] The results were achieved by close integration of all sources of information as opposed to cryptanalysis of Russian ciphers, although low and medium grade Russian ciphers were read. The ratio of general evaluation against pure cryptanalysis was about three to one which was due to the following:
- * Russian High Grade ciphers were generally unreadable, due to the use of one-time pads.
- * A large amount of information could be obtained from Russian military practices, movements of strategic reserves, chain of command, intentions to attack as well as including use of Indicators on ciphers, call-signs and a low standard of Russian wireless discipline.[10]
From an examination of the cryptographical processes of Russian security, Kona 1 appeared to have determined that one time pads were used for high grade ciphers, and a number of code books and recyphering tables were used for medium and low grade ciphers. Medium and low grade ciphers appear in most cases were within the capability of KONA 1 to be available for reading.[10]
Captain Roman Roessler, Chief Evaluator of KONA 1, and commanding officer of the Intelligence Evaluation Centre (German: Nachrichten Aufklaerung Auswertungsstelle) (abbr. NASS) of the KONA regiment, stated that even if identification of individual formations wasn't possible, KONA was still successful in formulating a picture of groupings and number of formations. As regards the Russian Rifle Corps and Divisions, KONA had to rely on other means to gather signal intelligence[11] KONA 1 successes may be considered overenthusiastic.[12]
Organization and Functions
KONA Regiment
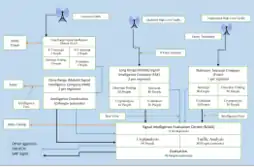
The purpose of a KONA regiment was to supply intelligence to the Staff (military) of the Army Corps, Armies and Army Groups. Each KONA unit consisted of a Regimental Evaluation centre and possibly 5 or 6 intercept and intelligence companies. The KONA regiment operated with the signal intelligence platoons operating close to the front line, with its companies situated close to army HQ and the main evaluation unit situated in the rear at Army Group Headquarters (abbr. HQ).
Close Range Signal Intelligence Companies (German: Nachrichten Nahaufklärungskompanie) (abbr.NANAK or NAK) were tasked with intercepting low level traffic. These were evaluated as they came in, with all intelligence passed to Senior Staff of their assigned Army Group as it became available, with all intercepts and immediate reports passed back to an evaluation platoon at company headquarters, for further evaluation.
Long Range Signal Intelligence Companies (German: Nachrichten Fernaufklärungskompanie) (abbr. NAFAK or FAK) intercepted high level traffic, undertook some immediate evaluation which was passed to Senior Staff, and also passed back reports and intercepts to the regimental Signal Intelligence Evaluation Centre (German: Nachrichten-Aufklaerungs Auswertestelle) (abbr. NAAS).
In 1944, the Signal Intelligence Battalion (German: :Nachrichten Aufklaerung Abteilung) (Abbr. NAA) was introduced into the organization of the KONA. These battalions were small administrative units, which acted to co-ordinate unit activities at Army level. Major Hertzer, Commanding Officer of KONA 1 stated that the NAA supervisors were generally elderly soldiers, who duty was to gather opinions and make small adjustments in close range signal, intelligence platoons, i.e. NAZ. Colonel Boetzel, head of the OKH/GdNA, stated that the NAA was not an effective improvement.[13]
Signal Intelligence Evaluation Centre (NAAS)
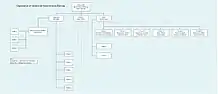
The Signal Intelligence Evaluation Centre (German: Nachrichten-Aufklärungs Auswertestelle) (NAAS) centre was situated close to an Army Group HQ[10] The NAAS functionality included evaluation and traffic analysis, cryptanalysis, collation and dissemination of intelligence.
- Four types of activity was included for the Evaluation and Traffic Analysis of intercepts:[14]
- Technical and tactical evaluation of (NAAS)
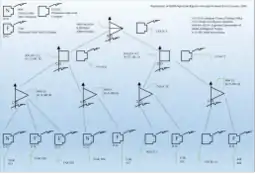
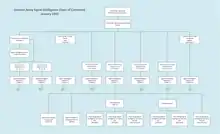
 Order of Battle Hierarchy of signal intelligence intercept unit, KONA 5, at the beginning of the Allied Normandy Landings Original Diagram created by Lieutenant Colonel (German: Oberstleutnant) Mettig
Order of Battle Hierarchy of signal intelligence intercept unit, KONA 5, at the beginning of the Allied Normandy Landings Original Diagram created by Lieutenant Colonel (German: Oberstleutnant) MettigThe NAAS centre was situated close to an Army Group HQ[10] The NAAS functionality included evaluation and traffic analysis, cryptanalysis, collation and dissemination of intelligence.
- Four types of activity was included for the Evaluation and Traffic Analysis of intercepts:[14]
- Technical and tactical evaluation of all identified intercepts, i.e. picked up by Long Range units.
- Processing of all unidentified intercepts. Traffic analysis from both long and short range units including intercepts which may not be from the enemy armies.
- Checking and tactical evaluation of reports from Short Range units.
- Traffic analysis, Direction finding evaluation, update of registry card index, NKVD evaluation and Russian Air force intercepts processing.
- Cryptanalysis in the NAAS primarily meant the solution of unknown systems, the study of developments in known systems, and work on NKVD ciphers and processes. The NAAS worked on 4-figure Russian ciphers.
- The NAAS was responsible for the dissemination of intelligence, passing its results to the Intelligence Officer of the associated Army Group, and also forwarding the intelligence to the Signal Intelligence Agency of the OKH/GDNA[15]
- The NAAS had a key position in the direction of coverage for interception. Through the chain of command, it controlled the intercept coverage for all lower units with co-ordination by staff of the headquarters of OKH/GDNA controlling everything else[16] Certain items were passed unprocessed straight to the GDNA cryptanalysis unit. Ciphers from the NKVD that were formatted using 5-figure groups were passed automatically to the GDNA cryptanalysis unit for additional cryptanalysis.[17]
- Four types of activity was included for the Evaluation and Traffic Analysis of intercepts:[14]
- Technical and tactical evaluation of (NAAS)
Stationary Intercept Company (FESTE)
The stationary Intercept Companies (1923–1939 German: Feste Horchstelle, 1939–1945 German: Feste Nachrichten Aufklaerungsstelle) (Abbr:Feste or more commonly FNAST) were designed to work at a lower level to the NAAS, i.e. that of the Army. The intercepts were designed in the pre-war period, and although they were retained, their traditional functionality and designation of being fixed (German: Feste Horchstelle) in a single location was redesigned to become semi-motorized for use in the East during the Russian campaign and later. Feste 10, the stationary company of KONA 1, operated close to Army HQ[18]
Feste 10 consisted of five sections, besides the HQ section. An intercept platoon, controlled by the NAAS,[19] covered unknown traffic in the 3500-5500 kHz band, fixed NKVD nets assigned by NAAS and those formations of mobile network traffic as directed by NAAS.[20] An evaluation section identified and reported unknown traffic. The study of unidentified intercepts was a primary function of the Feste.[21] A cryptanalysis section worked to identify cipher keys, translation of plain-text messages and solutions to cyphers.[22] The Feste also had a Direction Finding platoon, which provided resources on demand. Communications between the Direction Finding sites and the Regiment were provided by a Communications platoon, which passed results back to the NAAS via telegram or teleprinter.[22]
Long Range Intelligence Company (FAK)
These companies (German: Nachrichten Fernaufklaerungs Kompanie) (Abbr:FAK) were different from the Feste, in that they were more concerned to a greater degree with identified traffic. Like the Feste, they were semi motorized and were designed to operate close to Army HQ.[18] They were designed in a manner that each unit should be associated with each army staff covering an army section. In reality however, the operations of these types of companies, and indeed the Feste, took place further and further in the rear. The large amount of work that needed to be undertaken and became heaviest just at the time when safety precautions required a withdrawal, meant that it was found to be more practical to undertake work in the rear where it would be less frequently interrupted.
In gathering intercepts, the FAK's were directed by the cover control section of the Evaluation Centre (NAAS).[19] The traffic intercepts received by the unit was studied as fully as resources allowed. Plain-text messages were translated, with intercepts with known ciphers decoded by specialists attached to the unit. A card index section was maintained by the archivist. Those intercepts which couldn't be analysed via cryptanalysis were forwarded to the traffic analysis section of the NAAS.
Close Range Intelligence Company (NAK)

The Close Range Company (German: Nachrichten Nahaufklaerungs Kompanie) (Abbr:NAK), worked at Army Corps level. Its primary task was to intercept traffic and work on low-level 2, 3, and possibly 4 digit ciphers traffic close to the front lines.[23] Although the unit was designed to work at Army Group level, in practice such companies were also stationed by the commander of regiment with each Army as well.[24] In contrast to the Long Range Companies, these units were designed to operate by platoon.[18] The operation of each company was divided amongst four platoons which were, (German: Horchzug) which intercepted traffic, (German: Peilzug) for bearings and fixes on enemy transmitters, Evaluation (German: Auswertezug) and (German: Sendezug), which handled all communication problems.[25] The direction finding platoon whose organization was particularly elaborate, operated from tents.[26]
Normal direction finding operations for one company called for an average of eight out-stations, spaced 5 to 10 kilometres from each other and parallel to the front of one to several hundred kilometres. From HQ to the outstation was 20-30 kilometers. Each station was mobile and moved as the fighting moved. For communications wire would sometimes be available, but mostly it was wireless. A normal days operations used approximately 20 receivers, of different designs and types, according to the frequency range they listened too.[27] Antennas were of the usual inverted L type, averaging 60 metres in length, and from 10 to 12 metres high. Masts for antennas 8 metres high were always carried, but an effort was always made to find longer masts locally. Receivers were powered exclusively by batteries. Gasoline driven generators were used to power the transmitters.[28] Attached to each platoon was a small evaluation section, consisting of 1-3 evaluators[29] who generally operated out of a captured house or tent near the intercept station[25] with their results being passed to the Evaluation platoon of the company. Only the simplest systems were worked on at the NAK level, with the majority of the intercepts being passed to the NAAS, which studied the intercepts using cryptanalysis and well as for tactical intelligence derivable through traffic analysis.
Close Range Signal Intelligence Platoons (NAZ)
Each Close Range Company usually had two or three Close Range Signal Intelligence Platoons (German: Nachrichten Nahaufklaerungszug) (Abbr. NAZ), designed to work below the NAK but still at Army Corps level.
Signal Intelligence Battalion (NAA)
The Signal Intelligence Battalion (German: Nachrichten Aufklaerung Abteilung) (Abbr. NAA) was introduced into the organization of the KONA, in 1944, as a considered improvement on the NAK and FAK operational model of radio intercept. These battalions were small administrative units, which acted to co-ordinate unit activities at Army level. NAA supervisors were generally elderly soldiers, whose duty was to gather opinions and make small adjustments in close range signal intelligence platoons, i.e. NAZ. Colonel Boetzel, head of the OKH/GdNA, stated that the NAA was not an effective improvement.[13]
Operations
Direction Finding
Direction finding (D/F) was perhaps of the greatest importance in signal intelligence activities, as it enabled the location of the enemy. Its importance increased as Russian radio discipline, code and cypher security improved during the latter half of the war.[30] The Kona employed 5 personnel with each forward platoon with 50 D/F personnel stationed at Feste 10 (the long range intercept unit).[13]
The NAAS evaluation section received raw intercepts from the D/F sections of both the FAK and the NAK. The FAK sent requests not only to the long range but also the close range direction finding sites. Fak 617, which covered the Russian 1st Ukrainian Front, for example, sent its orders both to three or four long range direction finding sites and about 12 close range units. The D/F reported back using enciphered wireless signals.[30]
Long range D/F sets were located 200-350 kilometres behind the front line. Three D/F sets at a particular spot constituted a D/F group.[31] A supervisor who worked at Company level working in the intercept room issued requests. Through this means, simultaneous fixes could be taken by two and frequently by three sites.[32]
Close range D/F sets were located at the NAK platoon level. These sets received requests not only from the Long Range Companies but also the Close Range Headquarters.[31]
Direction finding techniques
The site chosen by the D/F unit had to be favourable for good radio reception and minimum magnetic declination. Each unit included 2-3 operators, one of whom received messages from other D/F teams, while the second acted as intercept operator, relaying intercepts back to the NAAS.[2] Two to three D/F sets in one place constituted a D/F Group where each set operated for a particular company. Results were reported back by W/T.[33]
The D/F operators had to acquire adeptness in rotating the loop antenna to the point of minimum volume, ascertaining the width of this band of minimum response, and computing the exact azimuth from the marginal readings. Moreover, D/F operations had to be carried out with exceptional speed, since often only one or two call signs or an acknowledgement lasting a few seconds could be intercepted. Extreme care had to be exercised to ensure the NAAS operators were not deceived. Each operator used a report form on which he entered information regarding the time, frequency, call sign, and fragments of intercepted messages, as well as the azimuths obtained.[2]
To dispatch D/F teams a transmitter at the intercept centre was used. The operator stated the frequency and call sign of the station to be located and the number of the D/F team, so that the azimuth thus taken could be later confirmed by checking. If no teletype communication was available, the D/F data was forwarded to the evaluation centre by radio.[2]
History of Kona Units
Kona 1
Kona 1 operated in the vicinity of Lviv, later Vinnytsia, then Poltava, then Reichshof and the towards the end of the war, the Czechoslovakia area.[34]
To Kona 1 headquarters were subordinated:[35]
- 1 Signal Intelligence Evaluation Centre - NAAS 1
- 1 Stationary Intercept Company - Fest 10
- 1 Close Range Signal Intelligence Company - NAK Preuss
- 2 Signal Intelligence Battalions - NAA 3 and NAA 4
To NAA 3 were subordinated:
- 1 Long Range Signal Intelligence Company - FAK 623
- 1 Close Range Signal Intelligence Company - NAK 953
To NAA 4 were subordinated:
- 1 Long Range Signal Intelligence Company - FAK 617
- 1 Close Range Signal Intelligence Company - NAK 954
Headquarters
The headquarters unit of KONA 1 which worked at Army Group HQ, consisted of the commandant of the KONA, his Adjutant, a Chief of Operations, a paymaster, a technical inspector, clerks and truck drivers. The following statistics show the breakdown of the HQ unit[36]
| Officers | Enlisted Men | Women | |
|---|---|---|---|
| Commander | 1 | - | - |
| Adjunct | 1 | - | - |
| S-3 | 1 | - | - |
| Paymaster | 1 | - | - |
| Technical Inspector | 1 | - | - |
| Clerks | 4 | 2 | |
| Truck Drivers | 9 | - | |
| 5 | 13 | 2 |
NAAS 1
The NAAS of KONA 1 has two major operation subdivisions: a section engaged in evaluation and traffic analysis, and a section for cryptographic activities. There was also an HQ section, a communication line section, a truck drivers section, a communication line section and a section for truck drivers. The number of personnel totalled 8 officers, 160 enlisted men and 50 enlisted women divided as follows:[36]
NAAS Section Officer Enlisted Men Women HQ 1 18 2 Evaluation 6 66 25 Cryptanalysis 1 42 - Communication - 21 23 Truck Drivers - 13 - 8 160 50
Feste 10
The Stationary Intercept Company, Feste 10, and the Long Range Signal Intelligence Companies, FAK 617 and FAK 623, were similar in the organization and operation. Each had a HQ Section, monitoring platoons, and evaluation section, a cryptanalytic section and a communication platoon. The difference between Feste 10 and the FAK were minor. Feste 10 was less mobile that the FAK, having eight truck drivers, instead of 12 and 16 assigned to FAK 617 and FAK 623. The following tables show the subsections and strengths of the Feste 10, FAK 617 and FAK 623.
The following tables show the subsections and strength of the Feste 10, FAK 617 and FAK 623 The following described the layout of Feste 10:[37]
FESTE 10 Section Officer Enlisted Men Women HQ 1 18 2 Evaluation 1 25 8 Monitoring Platoon 32 61 Cryptanalysis 1 42 2 Communication Platoon - 10 - Truck Drivers - 13 - D/F and Intercept - 50 - 3 158 73
FAK 617
The following described the layout of FAK 617:[37]
FAK 617 Officers Enlisted Men Women Headquarters 1 15 3 Monitoring and Intercept 1 91 - Evaluation 1 33 - Cryptanalysis - 20 - Comms Platoon - 23 - Truck Drivers - 16 - 5 198 3
FAK 623
The following table describes the layout of FAK 623:[37]
FAK 623 Officers Enlisted Men Women Headquarters 1 14 4 Monitoring and Intercept 1 83 - Evaluation 1 34 - Cryptanalysis - 16 - Comms Platoon 1 17 - Truck Drivers - 12 - 4 176 4
NAK 954
The Close Range SigInt Company, NAK 954, was also managed and split into a number of subsections.
The NAK operated by platoons, one platoon attached to each Army Corps.[31] The strength of the platoon was from 20 to 30 men, of which approximately 12 were used for radio telephone intercept, 2 in radio intercept, 4 in D/F and 3 in evaluation. The rest of the platoon compromised clerks, drivers and cooks. For NAK 953, Up to September 1944, it was subordinated to NAA 3 of KONA 1, at the time it was moved to the West, leaving behind its interpreters and cryptanalysts, who continued to serve on the eastern front.[10] NAK Benold, named after its commanding officer, was composed of specialists of various kinds who had been drawn from the SigInt companies subordinate to KONA 1. As a company, it formed part of NAA 3. NAK Preuss was formed from forces withdrawn from other units of KONA 1. This close range company was, in contrast to other companies, subordinated directly to KONA Headquarters.
NAK 954 Officers Enlisted Men Women Headquarters 1 41 - Evaluation 1 30 - Radio Receiving - 25 - Comms Platoon 1 18 - 4 Monitoring Platoons 4 112 - 4 226 -
NAK 953
Up to September 1944, NAK 953 was subordinated to NAA 3 of KONA 1, but at that time it was moved to the west, leaving behind only its interpreters and crypt analysts, who continued to serve on the Eastern front.[38]
NAK Benold
NAK Benold, named after its commanding officer, was composed of specialists of various kinds who had been drawn from the signal intelligence companies subordinate to KONA 1. As a company it formed part of the NAA 3.
NAK Preuss
NAK Preuss, taking its name as did NAK Benold, from its CO, was formed from forces withdrawn from other units of KONA 1. This close range signal company was, in contrast to other companies, subordinated directly to KONA HQ.
Kona 2
KONA 2 operated in Warsaw, Barysaw, Orsha, Vitebsk, Smolensk, Minsk, Grodno, then Szczytno, Gdańsk and finally Holstein.[34] The KONA 2 organization is not known in detail. It had the following order of battle:[10]
- 1 Signal Intelligence Evaluation Centre, NAAS 2
- 3 Signal Intelligence Battalions, NAA 6,NAA 7, NAA 8
- 1 Stationary Intercept Company, Feste 7
- 3 Long range Signal Intelligence Companies, FAK 610, FAK 619, FAK 622
- 3 Close range Signal Intelligence Companies, NAK 951,955,958
In February 1945, these components of KONA 2 were split; part of them remained with KONA 2, which was reassigned from Army Group North to Army Group Weichsel; part of them were attached to KONA Nord, which took the place of KONA 2 with Army Group North. The original components were divided between the two KONA in the following way:[39]
- KONA 2:
- 2 Long Range Signal Intelligence Companies, FAK 610, 622
- 1 Close Range Signal Intelligence Company, NAK 958
- 1 Stationary Intercept Company, Feste 7
- KONA Nord:
- 1 Long range Signal Intelligence Company, FAK 619
- 1 Close Range Signal Intelligence Platoon, NAZ Brutus
- 2 Close Range Signal Intelligence Companies, NAK 951, NAK 955
- 1 Signal Intelligence Evaluation Centre, NAAS 2
This remained the general structure until 28 March 1945, when by order of General Albert Praun to return KONA Nord units to KONA 2, except the Close Range Signal Intelligence Companies NAK 951, and NAK 955[39]
Kona 3
KONA 3 was composed of one NAA (10),[40] one FAK (possibly 611, which was transferred to the west under KONA 6 in October 1944),[40] one NAK, one FESTE. Nothing further is known about KONA 3, as it ended up caught by the Russians in a pocket in Kurland, a region in Latvia, towards the end of the war and captured intact by the Red Army[41][42] KONA 3 operated in Riga, Pskov and Courland where it was caught in the Courland Pocket.[34]
Kona 4
KONA 4 was subordinated to the Commanding Officer Southeast, OB Südost (German: Befehlshaber Suedost), who controlled the German Armies of the Balkans[43] These armies responsibility was one of an occupational force and there KONA 4 added to its normal task of intercepting long range traffic emanating from the Middle East and Africa, i.e. that of monitoring the traffic of the occupied Balkan countries. For this reason KONA 4 included no mobile Long Range Signal Intelligence Companies and only two mobile Close Range Signal Intelligence companies. The other units belonging to KONA 4 were NAAS 4, and two Feste, Feste 5 and Feste 6[43]
NAAS 4
NAAS 4 code name was HASSO, which stood for (German: Horchauswertestelle Suedost) (Listening from the Southeast), Intercept Evaluation Station Southeast[44] NAAS 4 was divided into the cryptanalysis section, a D/F section, a tactical and final evaluation sections.[45] The NAAS 4 unit has around 90 men, including interpreters, decoders, cryptanalysts, evaluators, draughtsmen, drivers, telephonist and wireless operators.[46]
Feste 5
Feste 5 was the former Army Fixed Intercept Station at Graz. The unit has the sections:
- HQ
- Radio intercept section.
- Radio operation and maintenance section for radio transmitter.
- Cryptanalysis section.
- Evaluation section for D/F activities.
The unit had a headcount of around 170 men and operated around 50 radio intercept sets. It had the usual mix of staff prevalent in KONA 1 Feste.
Feste 6
Feste 6 was the former Army Fixed Intercept Station at Tulln. It had a strength of around 130 personnel[46] and similar sectioned layout as Feste 5.
NAZ T
KONA 4 had two Close Range Signal Intelligence Platoons: NAZ T and NAZ W.
NAZ T consisted of 42 men, among them was Turkish linguists, cryptanalysts and interpreters.[46] NAZ T had the following layout:
- Platoon HQ
- Radio intercept station with 10 sets.
- Radio maintenance section
- D/F Platoon
- Cryptanalysis section for Turkish communications only
- Final evaluation section for D/F
NAZ W
NAZ W consisted about 80 personnel who specialized in monitoring internal Balkan radio traffic, and was based in Belgrade to collect and decode traffic of General Draža Mihailović and Marshall Josip Broz Tito.[46] It was organized as follows:
- Platoon HQ
- Radio intercept station.
- Radio maintenance section
- D/F Platoon
- Cryptanalysis section
- Final evaluation section for D/F
The KONA unit had a Radio Controlled Station, or Broadcast Monitoring Point (German: Rundfunkueberwachungstelle) which was part of KONA 4 until it was dissolved in 1942.[46]
Kona 5
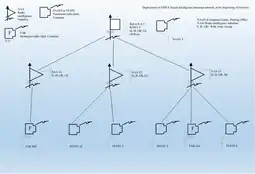
KONA 5 was located on the Western Front for much of World War II and was the only unit of that type located there, until the establishment of KONA 7 in February 1943. Before February 1944, the KONA 5 organization consisted of NAAS 5, Feste 2, 3,9 and 12, as well as two Long Range Signal Intelligence Companies, FAK 613 and FAK 624[47] Sometime after February 1944, KONA 5 was changed.[48] The reorganisation of KONA 5 follows the change in the German order of battle which took place on the western front in early 1944. Prior to that time, the western armies had been under command of Army Group D to which KONA 5 was attached. However, in early 1944, Army Group D was absorbed into OB West (German: Oberbefehlshaber West) which took control of three newly formed Army Groups on the western front, Army Group B, Army Group H and Army Group G. KONA 5 was reorganized so that it contained:
- Three NAA: NAA 12, 13 and 14. NAA 12 was attached to Army Group D, NAA 13 to Army Group B and NAA 14 to Army Group G[49]
In regard to the subordination of the six component parts of KONA 5 to the three NAA units, there is disagreement between the Combined Services Detailed Interrogation Centre publication[47] and a TICOM interrogation report.[40][50]
According to the TICOM report: Feste 12 combined with Feste 3 to form NAA 12; Feste 2 and 9 combined with FAK 613 to form NAA 12. There was no indication whether FAK 624 combined with other companies when it formed NAA 14.
Kona 5 organization remained constant throughout most of 1944. In late 1944, an attempt was made to centralize and strengthen the western field organization. A new senior communication intelligence officer (German: Hoeherer Kommandeur der Nachrichten Aufklaerung) (Abbr. Hoeh Kdr D Na) was established. The new Commander, Colonel Kopp was attached to OB West (German: Oberbefehl-shaber West) and was made responsible for all signal intelligence activities in the west[51] The western field organisation was strengthened by moving KONA 6 from the eastern front to the western front to join KONA 5. Both KONA units were subordinated to Colonel Kopp: KONA 5 was assigned to Army Group D, which controlled the German armies on the southern end of the western front, and KONA 6 was attached to Army Group B which controlled the German armies on the northern end of the western front[52]
With KONA 6 move to the west, KONA 5 organization was modified. The Signal Intelligence Battalions were reduced to two, NAA 12 and NAA 14. NAA 13 which had been composed to two Stationary Intercept Companies: Feste 2 and 9, and one Long Range Signal Intelligence Company: FAK 613, was taken from KONA 5, broken up and its individual components reassigned. Feste 2 was placed under direct supervision of Colonel Kopp; Feste 9 was shifted from Norway to Italy, where it fell under KONA 7; and NAA 12 with FAK 613 was assigned to KONA 6. KONA 5 was compensated for the loss of FAK 613 by the addition of FAK 626, which was taken from one of the eastern front KONA, (perhaps KONA 8) and brought to the western front.[40][47]
During Spring 1945, KONA 5 was organized as: One evaluation centre: NAAS 5, with two battalions: NAA 12 and NAA 14, one Stationary Intercept Company: Feste 12, one Long Range Signal Intelligence Company: FAK 624 which was subordinated to NAA 14, one Signal Intelligence Company: FAK 626. This was the organisation of KONA 5 until the capitulation.
-
NAAS 5
NAAS 5 was located close to Paris at Saint-Germain-en-Laye. The unit had about 150 personnel, consisting of interpreters, cryptanalysts, evaluators, Draughtsman, switchboard operators and telephonists, drivers, clerks. In addition, some women auxiliaries were available, particularly for telephonist and switchboard work. The internal organization of NAAS 5 is not known[48]
-
Feste 12
The unit was subordinated to NAAS 5 until early 1944, when it joined with Feste 3 to form NAA 12. Feste 12 organisation consisted of a radio intercept platoon, and a telephone communication unit. When it was attached to NAAS 5, Feste 12 has no cryptanalysis or evaluation personnel since this work was being done at NAAS 5. The strength of Feste 12 was estimated at 120 men and 30 women auxiliaries[53]
-
Feste 2
According to a prisoner's account[53] the organization of Feste 3, the former Army (Wehrmacht) intercept station at Münster, closely approximated Feste 3. It had a radio intercept platoon, a D/F platoon, and an evaluation platoon consisting of two sections: one for the evaluation of content of messages, content evaluation (German: Inhaltsauswertung) and one for the evaluation of traffic, traffic analysis (German: Verkehrsauswertung). In 1944, Feste 2 combined with Feste 9 and FAK 613 to form NAA 13. When NAA 13 was broken up in November 1944, Feste 2 was subordinated directly to the Senior Commander of Signal Intelligence in the West, Major General William Gimmler.
-
Feste 3
Feste 3 was the original Army intercept station at Euskirchen. Early in the war it had been subordinated to KONA 5. Administered independently in 1944, it combined with Feste 12 to form NAA 12. When KONA 5 was reorganized in the fall of 1944, Feste 3 was combined with the Long Range Signal Intelligence Company: FAK 626, which had been brought from the Eastern Front to form NAA 14. This organization was valid until the end of the war[54] The internal organization of Feste 3 is described by a liaison officer, Lt. Hans Lehwald, who was attached to it. He stated that it consisted of a radio reception platoon of approximately 70 receivers, and an evaluation platoon of 25-30 men. The evaluation was broken into section for traffic analysis, cryptanalysis, evaluation, D/F and filing section for diagrams of the nets, call signs, personalities, code names and D/F results[55]
-
Feste 9
Feste 9 was a Stationary Intercept Company formed in Frankfurt in the Spring of 1942 and sent to Norway in July of that year. It was first stationed at Trondheim, later in Bergen, and in the Spring of 1944 at Ski near Oslo. Between the summer of 1944 and the following winter, most of the personnel were moved to Italy and by Christmas 1944, there was nothing left of the unit in Norway[56] While in Norway, Feste 9 was organized along the lines of a Long Range Signal Intelligence Company, with a HQ platoon, an intercept platoon· or BO-120men, a D/F platoon, a radio reconnaissance platoon of about 20 men, and an evaluation section of about 30 men. The evaluation section had one subsection for the evaluation of message contents one for traffic, and one for cryptanalysis[56] When in Norway, Feste 9 was, subordinated to KONA 5. It can be surmised, however, that its connection with KONA was always more flexible than that other units because of its geographical position in Norway. When NAA 13 was broken up, Feste 5 remained under the supervision of KONA 5 until it was shifted to Italy under KONA 7[57]
-
FAK 624
FAK 624 was formed at Montpellier on 16 April 1943 and attached to KONA 5[54] In February 1944, FAK 624 was subordinated to NAA 14 of KONA 5, and in late Autumn it combined with Feste 3 to form the reorganized NAA 14.[52] The unit was composed of an intercept platoon and an evaluation platoon. For transport, FAK 624 is said to have approximately 85 vehicles with six special French radio trucks and trailers for D/F equipment. The strength of the company was roughly 250 men including interpreters, code clerks, cryptanalysts, radio intercept operations and 90 drivers.[54]
-
FAK 613
FAK 613 belonged to KONA 5, in so far as is known from its inception. In February 1944 FAK 613 combined with Feste 2 and Feste 9 to form NAA 13. When this battalion was broken up in late 1944, FAK 613 was reassigned to KONA 6, where it remained until the end of the war.[52] Little is known about the organization other than its organization paralleled that of FAK 624.[53]
-
FAK 626
FAK 626 was established in August 1943, trained until January 1944 and was activated in Winniza. Its original mission was originally the interception of traffic of the 1st French Army, and the 7th American Army and later that of the 1st, 3rd and 9th American Armies. It was subordinated to an eastern KONA, perhaps KONA 8 and was stationed in the Ukraine. In October 1944, FAK 626 was sent to Landau where it was tutored in western traffic and reorganized. In November 1944, it met FAK 624 at Landau, and both units were sent west to KONA 5 with which they remained until the end of the war.[58] The strength of FAK 626 on the Russian Front was around 250-300 men of whom 80-100 men were intercept operators, 10-15 D/F operators, 10-15 cryptanalysts, 5-7 translators, 10 were traffic analysts. The unit was greatly under strength on the Western Front.[59]
Kona 6
KONA 6 was created and activated as an eastern KONA at Frankfurt in 1941 and stationed in the Crimea to work in the Caucasian campaign. After that campaign, it was reassigned to work on the interception of Russian partisan traffic. This remained its task until the KONA was reassigned to work in the western front.
There is little information about what KONA 6 did while it was in the east. As a western KONA, it had two Signal Intelligence Battalions: NAA 9 and NAA 12.
NAA 9 had been brought from the east in November 1944. Subordinated to it were the Close Range Signal Intelligence Company: NAK 956, which was established in October 1944 and the Long Range Signal Intelligence Company: FAK 611, which had been brought from the east at the time.
NAA 13, which had been assigned to KONA 6 from KONA 5 with the Long Range Signal Intelligence Company: FAK 613. Subordinated to NAA 12 were also FAK 610 which had been brought from the east in November 1944; and NAK 953 which had been reassigned from the east also in October 1944.
- FAK 613. FAK 613 was given by KONA 5 to KONA 6 in late 1944. Nothing is known of the organization of this unit, but was likely the same as other Long Range Signal Intelligence Companies.[53]
- FAK 611. FAK 6111 was active in the Eastern front during the Russian campaign from June 1941. It was also stationed in Poland, where it was attached to Army Group Centre.[60] In November 1944, FAK 611 was moved to the western front and subordinated to KONA 6, NAA 9[52] Nothing is known about the size of FAK 611 on the eastern front. On the western front, it was small enough to occupy a house in Zutphen, the Netherlands. It consisted of 30-40 radio and telephone operators, 10 cryptanalysts and decoders, and 25 evaluators[61]
- FAK 610. FAK 610 was activated in 1940 for operations on the eastern front[62] Subordinated to KONA 2, it worked at Tilsit in September 1940 and later settled at Volkhov, where it intercepted Russian traffic. In November 1944, it was transferred to the western front where it was subordinated to NAA 13 of KONA 6[52]
It operated in Rostov-on-Don, Novocherkassy, Minsk, where it reorganized for partisan traffic. It disbanded in 1944, and was assigned to OKH/Chi at the Maybach I and II bunker in Zossen.[34]
Kona 7
KONA 7 was established in February 1943 and subordinated to the Commander-in-Chief South (OB Süd), Albert Kesselring who controlled the Armies in Italy. In 1944, KONA 7 was made up of:[63]
- 1 HQ Unit.
- 1 Signal Intelligence Evaluation Centre: NAA 7, with a code-name of Krimhilde
- 2 Stationary Intercept Companies: Feste 1 and Feste 9, with code-names of Monika and Astrid
- 1 Long Range Signal Intelligence Company: FAK 621 with code-name of Erika
- NAAS 7
NAAS 7 was organized into cryptography, cryptanalysis, evaluation. The evaluation sections included immediate, tactical, D/F, traffic, content, and final evaluation. The strength of the evaluation centre was about 150 men.[64]
- Feste 1
Feste 1, the former Army intercept station in Stuttgart, which had been stationed in Strasbourg in 1940, Brittany in 1941, and later that year in Montpellier, and later they moved to Italy and was attached to KONA 7 in 1943[64] The main task of Feste 1, was interception. No evaluation was done by the personnel who consisted of radio intercept operations, telegraph and telephone operators and D/F operators.[63]
- Feste 9
The origin of Feste 9 is described under KONA 5.
- FAK 621
FAK 621 was created in 1942 from the remnants of former 3rd intercept (German: Horch Kompanie) company: NA 56 at Bielefeld.[65] Most of the original FAK 621 was captured in the North African Campaign on 10 July 1942. The remnants of the company continued to work on Allied systems until May 1943, when the Allies captured the unit in Tunisia[66] Nothing is known of the organization of the company.
Kona 8
KONA 8, which was formed in October 1944, and was assigned to the Eastern Front Army Group South. It had one Evaluation Centre: NAAS 8, 2 Signal Intelligence Battalions, NAA 1 and NAA 2,[52] one Long Range Battalion: FAK 620, one Close Range Signal Intelligence Company whose identity is unknown, and one Stationary Intercept Company, either Feste 4 or Feste 8. It was known that Feste 8 attempted in the winter of 1942-3 to intercept Russian radio telephone traffic at Königsberg, but is not certain to what eastern KONA this Feste was assigned.[67]
KONA 8 operated in Odessa, Romania, Croatia, and finally Linz.[34]
FAK 620
FAK 620 had monitored western traffic on the Norderney Island from about August 1939 until it was sent to the eastern front and subordinated to KONA 8[58] Nothing more is known of the units.
Kona Nord
KONA Nord was created in February 1945 to serve Army Group North when KONA 2, which had been attached to that group, was transferred to Army Group Weichsel. From KONA 2, KONA Nord received NAAS 2, FAK 619, NAK 951, NAK 955, NAZ Brutus. This organization was valid until 28th Match 1945, when by order of General Albert Praun, KONA Nord was ordered to return to Army Group Weichsel all its components except the two Close Range Signal Intelligence companies: NAK 951 and NAK 955. These probably remained with KONA Nord until the capitulation.[39]
NAA 11
NAA 11 was a field unit unique in the General der Nachrichtenaufklärung organization. Although it was assigned to the 20th Mountain Army (German: Gebirgsarmee) under the command of Generaloberst Eduard Dietl. In matters of signal intelligence it was an independent unit subordinated directly to Intercept Control Station East (HLS Ost) acting in all respects like a Signal Intelligence Regiment.[68] Its units mission was to obtain signal intelligence from the Russians, mostly by the use of intercept.[68]
The original core of NAA 11 was the Long Range Signal Intelligence Platoon designated North (German:Nachrichten Fernaufklaerungszug Nord) (abbr. FAZ Nord) which operated in Finland after 1941. One 1 March 1944, FAZ Nord was merged with the Close Range Signal Intelligence Company, NAK 961 to form NAA 11, which increased the units strength from about 80 to 300.[68]
One of the most important accomplishments of NAA 11 Nord was the breaking of enemy codes, specifically Russian and later, Allied and Swedish codes. Russian codes, e.g. were built up from one another. Previous traffic and experience therefore were utilized from 1941 to 1945.[68] NAA 11 maintained an extensive card catalogue of some 6000 cards.[68]
The distribution of tasks of the NAA 11 Nord unit was as follows:
Job type No of Men Intercept Operations 200-250 men (75 sets) D/F operators 30 men Evaluation 40 Cryptanalysis 25 Own W/T traffic 30 men Drivers, cooks, mechanics 100+ men
NAA 11 Nord produced two types of reports:
The report was distributed to the Chief of Staff, Commander of XX 20th Mountain Army, General der Nachrichtenaufklärung by Teleprinter.[68]
In Autumn 1944, after Finland's capitulation, NAA 11 retreated to Norway.[68] In May 1945, when it was located as Gjøvik, Norway, it was ordered to turn over all its documents and paper to the 20th Mountain Army and to organize a group which would incorporate the experience and knowledge of the unit.[69] This party became known as The Norway Party and their published reports became TICOM documents I-55 and I-106.
Evaluation and cryptanalysis in a KONA Regiment
Evaluation in the NAAS
The main duty of the NAAS was to evaluate enemy traffic intercepted and passed to it by the Long Range and Close Range Signal Intelligence companies. Captain Roessler, Chief Evaluator of KONA 1, and Commanded Officer of the NAAS, observed that: "there were no prescribed rules for evaluation, and this fact, determined by the material dealt with, made the success or failure of the signal intelligence service a personal matter depending on the perspicacity and experience of a few specialists and persons operating in key positions".[70]
Evaluation in the NAAS was concerned with the observation and interpretation of known radio nets, the study of unidentified traffic and in the results of cryptanalysis. Roessler emphasized that in the case of KONA 1, "the interpretation of unknown traffic was...for a long term intelligence point of view, the chief evaluation problem".[71]
Comprehensive research work was necessary to systematize the evidence available, and the basic instruments of this systemic knowledge system was card indexes.[70][72] A fundamental principle, established after much difference of opinion, was that the smallest detail serving to characterize or identify the Allies W/T traffic should be carded: the resultant card index served the most varied purposes. The mass of material intercepted compelled this step; firstly as an Aide-mémoire, secondly a most careful record of all characteristics became increasingly urgent as, with increasing Russian W/T security, the sources available for interpretation became continually less numerous. Towards the end of the war, therefore, the card indexes were considerably extended, despite economies in personnel and material.[70]
In accordance with the above principles, Companies had to provide the most detailed reports. A smoothly functioning report system was the chief problem discussed at almost all meetings to consider organisation. A Long Range Signal Intelligence Company needed an average of 16 typists hours to get out its daily report for the NAAS.[70] The reporting system covered the following fields (whether in writing, by courier, or by teleprinter or telephone)
- Report on traffic of the W/T nets (call-signs, frequency, traffic workings, keys used, further characteristics)
- Report on content of signals.
- Technical Signals Reports
Reports of all the Companies, collated by the NAAS, gave a complete picture of the traffic intercepted during the day. The more important conclusions, i.e. those which had tactical value, deduced from traffic relations and content of messages, were collected in the daily Situation Report (German: Lagemeldung). The work of the NAAS hardly reflected in the Situation reports, as the intercept operator heard a great deal more than just enemy traffic he had been assigned to, and a greater percentage of all intercept traffic was no identified, the NAAS, had to deal necessarily with all the traffic of the Russian Armed Forces. The card indexes had to bear on this problem.[71]
Comprehensive Research work which served to generalise and/or systematise the detailed evidence was carried on from the same point of view. Further material which served in identification included:
- Names (including those heard in radio broadcasts)
- Cover-names.
- 5-figure characteristics.
- D/F results
- Map Coordinates
- Key usage
- Contents of decoded signals.
- Technical characteristics
The part played by decoded messages in the total success of Signal Intelligence diminished steadily towards the end of the war. Intelligence of greatest tactical value was drawn mostly from other sources, e.g. 5-figure characteristics,Map Coordinates. By and large, Signal Intelligence, gave an almost complete picture of the groupings of Russian forces, from the Fronts (Army groups_ via the Armies, down to the Corps level.[73]
The strategic mobile formations, i.e. Armour and Cavalry, were continuously covered. When formations could not be completely identified, perhaps because of camouflage measures, the overall groupings and number of available formations was still clear. Rifle Corps and divisions were usually better known to the NAAS centre through other sources, e.g. prisoners. In the overall picture, Infantry divisions, were not as interesting as the Senior HQs, and the mobile formations. It was essential for the NAAS that Signal Intelligence should observe events on the enemy's side which could be learned from no other angle.[73]
Card indexes
As NAAS 1 was the chief evaluation centre within the KONA 1 regiment: its card indexes had to be as comprehensive as possible, meaning collaboration with other regiments employed on the Eastern Front, i.e. KONA 2, 3 and 8 and with the GDNA East. An exchange system (new interpretations, corrections etc.) functioned smoothly with copied cards being exchanged via telegraph or courier, depending on urgency. The section which kept the card indexes updated was called the Abteilung Karteien ("Department of Card Files")[74] The following card indexes were kept:
- Personality Index: This index listed all officers and radio operators whose names were derived not only from radio but from all sources (interrogations, captured documents, etc.). All names were treated with caution due to the Russian propensity of using cover names. There was a special file for indexing these. When the entry was clarified, a suitable entry was made on the card. Example data: AIESKOWSKIJ, OBERST. Chief Signals Officer, 1st Ukrainian Front. (Mentioned on Wireless on 15/1/1935) or GWANOW, Major. Area 6th Pz. Army (18/2/'45, KONA 8)[75]
Unit Index: This file contained all information available from all sources on all Russian units. Each card was designed to list the following item: unit, commanding officer, chief of staff, components to which the unit was subordinate, subordinate units comprising the unit in question, location, date of first appearance, and sources of information.
Blocknot Index: Notes on Blocknots. The highest level code used by Soviet forces during World War II, in the East, was the 5-figure codebook enciphered with Blocknot book, where each page had a random sequence of numbers, organized in numbered rows and columns. There were two types or categories of Blocknots:
- The Individual in which each table of random numbers was used only once.
- The General in which each page of the Blocknot was valid for one day. The security of the additive sequence rested on the choice of different starting points for each message. In 5-figure messages, the blocknot was one of the first 10 Groups in the message. Its position changed at long intervals, but was always easy to re-identify.[76] The Russians differentiated between three types of blocks:
- The 3-block, DRIERBLOCK also called I-BLOCK, i.e. individual block, that could be used and read only between two wireless telegraphy stations on one net.
- The 6-block, SECHSERBLOCK, also called Z-BLOCK, i.e. circular block, that could be used and read, between all W/T stations in a net.
- The 2-block, ZWEIERBLOCK, also called the OS-BLOCK, used only in traffic from lower to higher formations.
The Chi-number was the serial numbering of all 5-figure messages passing through the hands of the Cipher Officer, starting on the first of January and ending on thirty-first December of the current year. It always appeared as the last group in an intercepted message, e.g. 00001 on 1 January, or when the unit was newly set up. The progression of Chi-numbers was carefully observed and recorded in the form of a graph. A Russian corps had about 10 5-figure messages per day, and Army about 20-30 and a Front about 60-100. After only a relatively short time, the individual curves separated sharply and the type of formation could be recognized by the height of the Chi-number alone.[77]
Blocknot Index: Both Blocknots and Chi-numbers were contained in the same index. A careful recording and study of blocks provided the positive clues in the identification and the tracking of formations using 5-figure codes. The index was subdivided into two files: one, the search card index, contained all blocknots and chi-numbers whether or not they were known; the other, the unit card index, contained only known Block and Chi-numbers. Inspector Berger observed that the two files formed: "The most important and surest instruments for identifying Russian radio nets, known to him.".[76]
Key Index: (Schluessel) This index contained all solved keys, irrespective of the areas in which they were used. They were arranged according to the German designation of the Russian keys. The German system of key designation includes a self-evident description of the code plus an allotted number, e.g. R4ZC 1800: meaning 4-Zahlen Code 1800/Russian 4-figure code 1800/333 The 2 and 3-figure keys were peculiar to definite formations and with this certain inferences about the formation in question could sometimes be made on the basis of the key alone.[76]
Call Sign Index: All call signs picked up on the entire Eastern front, known or unknown, were listed in this index, which showed not only the call signs, but also the connection in which it previously might have appeared.[77] The index was fully cross-references and was relied upon not only for spot identification of call-signs but for building new call-sign blocks.[78] Each card had a reference, the Network No.
Cover Name Index: The Russian Soviet forces used cover names abundantly, not only for units, but for common military expressions and tactical measures as well. Some were so consistently used that all disguise was lost, and they became accepted expressions. On the whole they presented no great difficulty and could usually be interpreted successfully.[79]
- Example хозяиство means Unit.[79]
All cover names obtained were scrupulously recorded by the Index Section. In many cases nearly complete cover tables were reconstructed from the various Russian fronts.[80]
Coordinates Index: The map coordinates derived by the solution of Russian map reference systems were recorded in this index, the co-ords being arranged both by the system and by the unit making use of the system.[80] It is significant that even though the coordinate system might not be understood, the method itself might be enough to furnish important clues facilitating the tracking of a particular formation.[81]
Direction Findings Bearings. This file consisted of a listing of the various bearings on each Russia radio station obtained through direction finding, and helped the NAAS to estimate the value and significance of the bearings.[82] Direction finding became increasingly important as one of the branches of signal intelligence, as Russian wireless discipline and cipher security became better and better as the war progressed. D/F requests to fix a W/T station by long range D/F within 15 km, or by close range D/F of about 2,3 km.[82]
Air Traffic Index: Russian Air Traffic was frequently picked up by operators assigned to search missions. In order to spot this intercept as Air traffic, a catalogue of its characteristics was necessary; and to accomplish this, a special index was set up in the NAAS. In this index were recorded not only the statistics derived from German Army interception of Air traffic, but also data supplied by units of the Luftwaffe (Sigint Abteilungen III/353 Luftflotte 4 and II/353 Luftflotte 6). The statistics gathered were passed to the Long Range Signal Intelligence Companies (FAK), which were likely to pick up Air traffic. The companies did not have separate air data indexes, but kept the data in the Army card index.[83]
In order to insure the most comprehensive indexes possible, liaison was maintained laterally between the NAAS and KONA 1 and the other regiments on the Eastern front. Full collaboration was effected also with OKH/GdNA. A system for exchanging current information, new interpretations, corrections, etc., operated smoothly, the data being passed by telegraph or courier depending upon the urgency of the item in question.[74]
Below the level of the NAAS, card index were extensively used; but they were less comprehensive, being only as complete as the company cover assignment permitted.[84] Regarding the card index in general, Roessler made a significant and characteristic observation, emphasizing that while the card indexes formed the indefensible material basis for evaluation, memory, experience and perspicacity of the individual evaluators lent the spark.[70]
Evaluation in the Feste
Evaluation in the Feste was the matter of identifying and interpreting unknown traffic, the interception of which was its particular function.[85] Some characteristics of Russian communications facilitating identification have been discussed in the preceding section. The systematisation of this work as carried on by the Feste Evaluation Sections showed how the identifying elements were studied at this level.
- The first task of the Traffic Evaluation Sections[86] was to work up the information into a network diagram, which not only represented the net structure but listed all pertinent information and formed the basic medium studied. The diagram contained:
- The net number.
- The date
- Traffic workings with call signs.[86]
- The number and kind of messages (if any) sent.
- The Direction finding number
- Block numbers and Chi-numbers on any 5-figure messages.
- Short plain text messages when available.
- Study of the network diagram in the 5-figure section (In the case of a 5-figure message having been picked up).[86]
- Identification of the W/T station sending the 5-figure message was the first step. The Blocknot and chi-numbers were studied and checked against the previously indexed or charted data in the index cards archive.
- The BLOCKNOT with almost the same number in the index.
- Identification by CHI-number alone (or in conjunction with the BLOCKNOT) checked against the Chi-number graph.[86]
- Identification of general class, e.g. Army traffic) by other 5-figure characteristics.
- All diagrams passed through the Traffic Analysis Section where the network diagrams were studied.
- General scrutiny of composition of call signs.
- Determination of area covered by net (Front, Army) comparison of call signs used with 'Basic Book for Allotment of Call-Signs' (German: Hauptverteiler)
- Recording and collecting of call signs still that were unclarified, in order to recover new call sign systems.[87]
- Checking of the network diagrams and messages against the card indexes of names, cover-names and cover-numbers.
- Identification of names and numbers by means of the index;hints for interpretation already entered on the network diagram taken into account.[86]
- The network diagrams were passed to the Direction Finding Evaluation Section,[88] which determined by the location of the fixes whether the intercept was likely to be, e.g. Army (near the front) or Air Force; or Line of Communication traffic, in the rear.
- Does the D/F fix, if any, point to an area near the front? If so, probably Army traffic.
- Does the D/F fix, if any, point to the rear area? If so, Air Force, or Line of Communication traffic.[86]
- The diagrams went finally to the Final evaluation or Fusion Section, where the results entered on the diagram by the various sections were weighted and considered in the light of information passed to the Final Evaluation unit by the Cryptanalysis section. The findings guided modification of the cover towards dropping the less important traffic and placing more sets on the interesting circuits.
- Decision on the identity of the traffic, taking into consideration:
- the balance of the results entered on the network diagrams by the various sections.
- results obtained by the cryptanalysis section.
- Reports to NAAS on:
- identified traffics.
- tactical information derived from the messages.
- Guidance for interception:
- Cover of less interesting traffic suspended.
- Special attention to more interesting traffic ordered.
The traffic identified by the Final Evaluation unit was reported to the NAAS, together with the tactical information derived from the messages. The findings guided modification of the cover towards dropping the less important traffic and placing more sets on the interesting circuits.
Evaluation in the FAK
The Evaluation Section in the FAK was apparently organized like that in the Feste, although the relative dearth of evidence available precluded drawing a close parallel. Presumably it differed in function from the Evaluation section in the FAK and worked on identified traffic as well.[89]
As in the case of the Feste, the basic document of evaluation was the network diagram, prepared by the Traffic Evaluation section. This diagram included all evidence by which the station in question had been identified (in the case of 5-figure traffic, the Blocknots and Chi-numbers) and other significant data. Apparently, as was the case of the Feste, this diagram parsed through various sections devoted to D/F evaluation, traffic analysis, work on unidentified traffics, content evaluation,[90][89] and finally to fusion or final evaluation.[89]
Cryptanalysis in the KONA
The details of cryptanalysis performed by the field units are discussed in Russian Cryptanalysis. Because of the importance of the field in the total evaluation, however, it is pertinent to note here the organization and function of the sections carrying out this work at KONA level.
NAAS
The cryptanalysis in the NAAS was performed by a special section separate from the Evaluation and Traffic Analysis sections. The cryptanalysis section totalled fewer than 60 people. Although the desired level was 60 personnel, it was never reached, despite increasing difficulties in Russian Keys which called for more and more specialists and assistants.
Cryptanalysis in NAAS 1 was accordingly, subdivided into the following sections:[91]
- 2-figure codes and cyphers
- 3-figure codes and cyphers
- 4-figure codes and cyphers
- New developments
- Analysis
- NKVD
- Code building (expansion) (German: Code-Ausbau)
- P/L text scrutiny
- Organisation[92]
The cryptanalysis section had the following tasks:[91]
- To collect and work on the traffic which the companies could not deal with, whether because of lack of material or preoccupation with more important systems.[91]
- To test and check doubtful solutions passed up by the companies.[91]
- To establish whether keys broken by the companies were the first examples of their kind; to complete them and put them in a handy workable form, i.e. basic form, and to assign a number to each key appearing in the area of the regiment.[91]
- To pass back down all solved key systems to companies who might be concerned.[91]
- To assign a number to each key appearing in the Regiments area.[91]
- To work on NKVD signals.[91]
Sections 1 to 3 analysed the relevant material in both raw and processed state: corrected mistakes in the Signals companies solutions, i.e. signals on which no work had been done (at Company level) were, if there was sufficient material, passed to the section dealing with New Developments. There were also responsible for checking the solutions offered in their respective (2,3, and 4-figure) fields.[91]
The New Developments section did the real cryptanalysis. It normally concentrated on difficult systems which the Signal Companies had neither time nor man-power to deal with adequately, if at all.[91]
The Analysis section consisted, in the main, of mathematicians and its work was of mathematical, systematic or analytic nature:[91]
- Work on 2,3, 4-figure Addresses.
- Work on 5-figure Signals, letter systems (transposition, Stencil).
- Examination of Signals with practice traffic characteristics.
- Reduction of solved keys to a basic form.[91]
Intercepted NKVD signals were worked on in the NKVD section of the NAAS, if they originated in the Regiments area. The remainder were sent by courier to LNA.[91]
The solved keys were passed, as necessary to the Book-building section (German: Ausbauabteilung) to be completed. This section worked in close contact with the analytic section, where a commonality of tasks, that of establishing the basic form of the key, existed.[91]
The section responsible for P/L text scrutiny investigated questionable translations, corruptions and abbreviations.[91]
FESTE AND FAK
The function and organisation of cryptanalysis in the long range companies, both Feste and FAK, appears to have been much the same in each. On paper, cryptanalysis at company level was a part of the evaluation platoon, in contrast to its independent position as a separate section in the NAAS.[93] It appeared to have functioned independently, in practice, because of the special nature of the work. The evidence indicated there may have been 15-20 people engaged in cryptanalytic work in the company evaluation platoons.[94]
- It was the task of company cryptanalysis not only to solve systems, to recover ciphers, to decode already known procedures, and/or to translate all this material, but also to contribute to the identification and interpretation of traffics on the basis of keys employed...[The cryptanalysis section] cooperated closely with cryptanalysis of the NAAS, but was so organised and equipped that it could work on most messages itself. Ltn. Harry Loeffler (FESTE 10)[95]
The cryptanalysis group was divided into separate sections for plaintext message translation, 2,3,4-figure traffic, with a separate section for each, and a general section which kept card indexes and lists, and performed certain administrative duties. These sections, besides being responsible for the solution of new systems, the recovery of additive, and the decoding of solved systems, played an important part in traffic identification through a study of the keys employed.[95] The key indicators, which Russia ciphers placed at the beginning and often at the end of the messages, were arranged by the numerical designation arbitrarily assigned by German staff to Russian keys in an index file.[96]
Cryptanalysts relied heavily upon the card indexes (described above) in their work, and also had at hand graphic and statistical presentations of signal letter, arbitrarily, and trigraphic frequencies, and lists of pattern words.[96]
They cooperated closely with the personnel engaged in the final evaluation section, often passing notes with the translated messages calling the attention of the evaluations to the key employed on the message, or to peculiarities which might have a significance when viewed in relation to the total data. Moreover, the cryptanalysts kept in touch with those responsible for intercept, to the end of obtaining the best possible copy for the new systems.[97]
Reports resulting from Evaluation
The finding of the intelligence units were passed to the operating agencies in various reports, and the intelligence contained therein was made available by an efficient reporting system. Captain Roessler observed that:
- a smoothly functioning report system was the chief problem discussed at almost all meetings to consider organisation.[70]
The companies were required to provide highly detailed reports.[70] They had to exercise their own judgement, showing initiative and intelligence in selecting the items to be passed on. A great deal of material was never reported at all but simply went into the card indexes of the companies. The companies had to distinguish urgent from routine items, and the NAAS frequently rebuked the forward units for a failure to send back in a flash what they had allowed to get through only in a routine report.[98]
The NAK maintained an evaluation platoon at Company HQ which correlated and interpreted the materials from other platoons, and reported the findings laterally to Army Corps command staff and upward to the NAAS.[99][100]
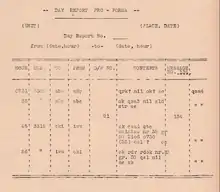
The basic technical report at company level was the Day Report made by the intercept operators, listing all traffic head on the frequencies monitored. There were columns for recording the time of intercept, the frequency upon which the traffic was taken, the call signs to and from, the contents of the transmission, the intercept number and remarks. All intercept operators made similar logs, which gave a picture of the total traffic carried on a particular link or network.
These logs provided the company evaluation sections with the subject matter studied in drawing up their Situation Report.[101] A typical Situation Report described the deployment and status of identified Russian units and reported any appearance of a new unit.[102]
The reports issued by the FESTE and the FAK were much the same. These included:[103]
- Twice-daily Network Reports (German: Netzmeldungen)
- Advance Reports (German: Vorausmeldungen or Sofortmeldungen)
- Daily Situation Reports (German: Tagesmeldungen) for a summary of the days Advance Reports and all less important data.
These reports were sent to the NAAS for further interpretation and significant intelligence items were then passed laterally to the Armies.[103] A long range company needed an average of 16 typist hours to get out its daily report for the NAAS.[70]
The Feste on the Eastern front issued in addition to the reports listed above a type of report known as the 5-figure offer was to assure the maximum exploitation of information available, and in effect constituted invitations to all KONA's to check the data in these reports with their own files. They listed all current data derivable from the external characteristics of messages consisted of 5-figure groups.[104]
The section at the NAAS for technical and tactical analysis collated and combined the significant findings from all these reports with the data at hand, passed material not immediately expoitable to the various specialists in the NAAS for the further squeeze and passed its combined report to the Army Group.[104] Roesser referred to the daily Situation Reports issued by the NAAS as a Location Report (German: Lagemeldung).
Information furnished by members of In 7/VI showed that the Signal Intelligence Reports issued by the Evaluation Centres of some regiments were called Radio Position Messages Report (German: Funklagemeldungen).[105] These consisted of four component reports:
- Direction finding reports (German: Peilmeldungen)
- Radio traffic reports (German: Betriebsmeldungen)
- Radio clear text reports (German: Funkmeldungen)
- Radio code-text reports (German: Verkehrsnachrichten)
These reports went beyond In 7/VI and were passed to the Army Group Commander as well as to the Army High Command the other echelons and commands on a distribution list of 14 listings.[105]
Notes
- "Volume 4 - Signal Intelligence Service of the Army High Command" (PDF). NSA. Retrieved 12 November 2016.
 This article incorporates text from this source, which is in the public domain.
This article incorporates text from this source, which is in the public domain. - Praun, Albert (1988) [1950]. German Radio Intelligence: A Lesson in COMSEC. Communications Security Establishment.
 This article incorporates text from this source, which is in the public domain.
This article incorporates text from this source, which is in the public domain. - Pahl, Magnus (17 January 2013). Fremde Heere Ost: Hitlers militärische Feindaufklärung. Links, Ch. p. 417. ISBN 978-3-86284-203-2. Retrieved 14 September 2017.
- Peter Matthews (2 September 2013). SIGINT: The Secret History of Signals Intelligence in the World Wars. History Press. pp. 142–. ISBN 978-0-7524-9301-5.
- I-23, Section 1
- IF-10, Page 10
- IF-10, Page 4
- I-19b Report on Interrogation of Kommandeur der Nachr. Aufkl. 1 (KONA.) at Revin, France, June 1945
- I-67, Page 3
- I-19b, Page 1
- I-19b, Pages 14-15
- I-19g, Pages 3-4
- I-19g, Page 5
- I-19b, Page 6
- I-19g, Page 7
- DF-18, Page 18
- I-19g, Page 8
- I-19g, Page 6
- DF-18, Page 82
- I-19b, Page 3
- I-19b, Page 3-4, 19-20
- I-19b, Page 4
- I-19h, Page 2
- I-19g, page 1
- I-62, Page 4
- I-62, Paragraphs 8-10
- I-62, Paragraph 9
- I-62, Page 9
- I-19b, page 2
- I-19b, Page 38
- I-19b, Page 2
- I-173, Page 34
- I-19b, p. 2
- I-116 p.8
- I-198, Page 5
- IF-40, Page 12
- IF-40, Page 13
- I-19b, p. 1
- DF-9
- I-76
- I-116, Page 8
- Rezabek, Randy (27 July 2012). "TICOM: The Last Great Secret of World War II". Intelligence and National Security. 27 (4): 513–530. doi:10.1080/02684527.2012.688305. S2CID 154706572.
- IF-171
- IF-171, Page 1
- IF-171, Page 2
- IF-171, Page 3
- IF-127
- IF-127, Page 2
- I-76 - Appendix
- The CSDIC report describing the group of the six components parts indicate the FAK 624 combined with Signal Intelligence Platoon 12 to form NAA 12; Feste 2 and Feste 12 combined to form NAA 12; Feste 613 combined with a Short Range Intercept Company, NAK 965, to form NAA 14. Feste 3 and Fest 9 were left as independent units to be administered by the Commander
- IF-123, Page 6
- I-76, Appendix
- IF-127, Page 4
- IF-127, Page 3
- I-76, Page 2
- IF-120, Page 6
- IF-144, Page 2
- I-76, Page 3
- I-76, Page 4
- I-55, Page 4
- I-74, page 2
- I-62, Page 3
- IF-172
- IF 172, Page 2
- IF-126, Page 10
- I-78, Page 9
- IF-123, Page 3
- I-55, Page 5
- I-55, Page 3
- I-19b, p.13
- I-19b, p.14
- I-19g, p.3
- I-19b, p.15
- I-19b, p.16
- Report No. 8 by Inspector Georg Berger in charge of document in KONA 1. I-19b, pp 16-18
- I-19b, p. 16
- I-19b, p. 17
- I-19b, p. 36
- I-173, p.25
- I-19b, p.18
- I-19g, p.10
- I-19b, p.38
- I-19b, p.52
- I-19b, p.10
- I-19b p.4
- I-19b, Report No 9 by Ltn Hans Boskam of Feste 10. pp. 19-20
- The source did not make clear whether this function was performed in the Traffic Analysis Section.
- Endauswertung I-19g, p.3
- I-19b, p.5
- The section concerned with content evaluation worked on all readable messages, identified places, names and cover-names...and sees to the immediate forwarding of all important messages to the NAAS
- I-19b, Report 5, p.9
- I-19b, Report 5 pp.10-11
- I-19b, Report 6, p.6
- I-19b, p.11
- I-19b, Report No. 6. pp. 11-12
- I-19b, Report No. 23, p.41
- I-19b, p.12
- I-19g, p.7
- I-19g, p.5
- I-19b, p.22
- I-173, p.24
- I-19b, pp 21-23
- I-19g, p.8
- I-19b, p.8
- IF-105, p.4
References
- TICOM I-23 Interrogation of Major Ernst Hertzer of Army Signals Intelligence Service (PDF), TICOM, 18 June 1945, retrieved 27 February 2017
- TICOM I-62 Field Interrogation of Paul Raatz of the German Army Signals Intelligence (1933-1945) (PDF), TICOM, 19 August 1945, retrieved 2 February 2017
- TICOM I-19ab Report on Interrogation of KONA 1 at Revin, France, June 1945 (PDF), TICOM, retrieved 2 February 2017
- TICOM I-19c Interrogation of KONA 1 - Annexe 1 Report on Russian Ciphers (PDF), TICOM, retrieved 2 February 2017
- TICOM I-19d Interrogation of KONA 1 - Annexe 1 Figures I to XVII (PDF), TICOM, retrieved 2 February 2017
- TICOM I-19f Interrogation of KONA 1 - Annexe 2 Traffic Analysis (PDF), TICOM, retrieved 2 February 2017
- TICOM I-19g Interrogation of KONA 1 - Annexe 3 German Army (Eastern Front) SIGINT Organization and Method (PDF), TICOM, retrieved 2 February 2017
- TICOM I-67 Paper of Dr. Otto Buggisch of OKH/IN. 7/VI and OKW/Chi on Cryptanalytic Machines (PDF). TICOM. Retrieved 2 February 2017.
- TICOM I-76 Prisoner of War Interrogation Reports (PDF). TICOM. Retrieved 25 February 2017.
- TICOM DF-9 Translation of OKW/Chi Activity Report 1 January 1944 – 25 June 1944 (PDF), TICOM, retrieved 27 February 2017
- "TICOM I-198 Short Brown List, July 1946" (PDF). TICOM. Retrieved 11 March 2017.
- "TICOM I-78 Interrogation of Oberstlt. Mettig on the History and Achievements of OKH/AHA/ln 7/VI" (PDF). TICOM. 15 May 1945. Retrieved 21 March 2017.
- "TICOM I-55 "Interrogation of Seven Members of NAA 11"" (PDF). TICOM. 12 July 1945. Retrieved 21 March 2017.
- TICOM I-173 Report by the Karrenberg Party on Russian W/T 16th December 1945 (PDF). TICOM. Retrieved 8 September 2017.