Mass surveillance in Australia
Mass surveillance in Australia takes place in a number of network media including telephone, internet and other communications networks, financial systems,[1] vehicle and transit networks, international travel, utilities, and government schemes and services including those asking citizens to report on themselves[2][3] or other citizens.
| Part of a series on |
| Mass surveillance |
|---|
| By location |
Communications
Telephone
Australia requires that pre-paid mobile telecommunications providers verify the identity of individuals before providing service.[4][5]
Internet
According to Greens Senator Scott Ludlam, Australian law enforcement agencies were issued 243,631 warrants to obtain telecommunications logs between July 2010 and June 2011, which vastly overshadowed the 3500-odd legal intercepts of communications.[6]
We've already taken some pretty dangerous steps in this country towards the surveillance state, and not that many of us are either interested or aware that it's going on, including people like me who should know better... Our friend and ally the United States is transitioning quite rapidly into an authoritarian state.
In 2013 it was reported that under Australian law state, territory and federal law enforcement authorities can access a variety of 'non-content' data from internet companies like Telstra, Optus and Google with authorisation by senior police officers or government officials rather than judicial warrant, and that "During criminal and revenue investigations in 2011-12, government agencies accessed private data and internet logs more than 300,000 times."[7]
Google's transparency report shows a consistent trend of growth in requests by Australian authorities for private information, constantly rising approximately 20% year-on-year. The most recent published volume for the period ending December 2013 indicates a volume of around four individual requests per calendar day.[8]
Telstra's transparency report for the period 1 July - 31 December 2013 does not include requests by national security agencies, only police and other agencies. Nevertheless, in the six-month period 40,644 requests were made, 36,053 for "Telstra customer information, carriage service records and pre-warrant checks" (name, address, date of birth, service number, call/SMS/internet records. Call records include called party, date, time and duration. Internet information includes date, time and duration of internet sessions and email logs from Telstra-administered addresses[9]), 2,871 for "Life threatening situations and Triple Zero emergency calls", 270 for "Court orders", 1450 for "Warrants for interception or access to stored communications" (real time access): an average of around 222 requests per calendar day.[10]


In 2013 more than 500 authors including five Nobel prize winners and Australian identities Frank Moorhouse, John Coetzee, Helen Garner, Geraldine Brooks and David Malouf signed a global petition to protest mass surveillance[11] after the whistleblower Edward Snowden's global surveillance disclosures informed the world, including Australians, that they are being monitored by the National Security Agency's XKeyscore system and its boundless informant. Snowden had further revealed that Australian government intelligence agencies, specifically the Australian Signals Directorate, also have access to the system as part of the international Five Eyes surveillance alliance.[12]
In August 2014 it was reported[13] that law-enforcement agencies had been accessing Australians' web browsing histories via internet providers such as Telstra without a warrant (Optus confirmed that they cooperate with law enforcement, and Vodafone did not return a request for comment). The revelations came less than a week after government attempts to increase their surveillance powers through new legislation allowing offensive computer hacking by government intelligence agencies, and mere months after outrage surrounding the government's offer to share personal information about citizens with Five Eyes intelligence partners.[14]
As of August 2014, no warrant is required for organisations to access the so-called 'metadata' information of private parties. This is information regarding "calls and emails sent and received, the location of a phone, internet browsing activity. There is no access to the content of the communication, just how, to or from whom, when and where." Under current law many organisations other than federal, state and territory police[15] and security agencies such as ASIO[15] can get access to this information, including "any agency that collects government revenue",[6] for example the RSPCA,[6][15][16] the Australian Crime Commission, the Australian Securities and Investments Commission[15] (though reportedly temporarily removed from the list),[15] the Australian Tax Office,[15][17] Centrelink,[17] Medicare,[15] Australia Post,[15][17] the Australian Fisheries Management Authority,[6] the Victorian Taxi Services Commission,[6] the Victorian Transport Accident Commission,[6] WorkSafe Victoria,[15] local councils[15][16] and foreign law enforcement agencies.[16]
In the 2013-2014 financial year there were over half a million disclosures of metadata to agencies.[17]
The Australian Communications and Media Authority provides instructions for internet service providers and other telecommunications providers about their law enforcement, national security and interception obligations.
During the 2015-2016 financial year 712 warrants were issued for access to stored communications,[18] 3,857 interception warrants were issued, and 63 enforcement agencies were granted 333,980 authorisations for metadata access.[19]
2014 proposals
A range of proposals are under discussion that affect surveillance of the population by government in conjunction with commercial service providers.
Hacking powers
The proposals seek to give the Australian Security Intelligence Organisation (ASIO) the right to hack into computers and modify them.[20]
Single computer warrant to become umbrella surveillance
The proposals seek to give ASIO the power to spy on whole computer networks under a single computer-access warrant.[20]
Spying on citizens abroad
The proposals seek to give the Australian Secret Intelligence Service (ASIS) the power to collect intelligence on Australian citizens overseas.[20]
Law against media and whistleblowing
Section 35P of the proposals seeks to create a new criminal offence, with a maximum penalty of 10 years imprisonment, for revealing information about so-called 'special intelligence operations'. There are no exceptions listed, and the law would apply to journalists even if they were unaware that they were revealing information about such an operation. Shadow Attorney-General Mark Dreyfus called the measure "an unprecedented overreach".[20]
Mandatory data retention
Mandatory data retention for two years of data relating to the internet and telecommunications activity of all Australians is currently under discussion.[16][20]
I must record my very grave misgivings about the proposal; it seems to be heading in precisely the wrong direction.
On Tuesday, August 5, government Communications Minister Malcolm Turnbull complained about "waking up to newspaper headlines concerning the government's controversial plan for mandatory data retention", stating the government "risked unnecessary difficulties by pushing ahead with the data retention regime without fully understanding the details". In 2012, Turnbull had opposed mandatory retention.[21]
On Friday, August 8, Australia's federal privacy commissioner, Timothy Pilgrim, stated he felt it remained "unclear" exactly what data was to be retained, and that "there is the potential for the retention of large amounts of data to contain or reveal a great deal of information about people's private lives and that this data could be considered 'personal information' under the Privacy Act".[21]
The government's proposal on data retention raises a number of important issues and so it is important that there is an opportunity for public consultation and debate on these proposals once the detail is available.
Later in the month, the head of Australian Security Intelligence Organisation (ASIO) appealed for access to private citizens' data on the grounds that commercial entities may already be collecting it.[22]
For the life of me, I cannot understand why it is somehow correct for all of your privacy to be invaded for a commercial purpose but I am not allowed to do it for the purpose of saving your life.
— David Irvine, ASIO chief, 22 August 2014
On February 19, 2015 the Australian Broadcasting Corporation's Radio National program Download This Show broadcast an interview with a former police employee who had worked extensively with metadata, on condition of anonymity. The former employee was quoted as feeling the proposed system was open for abuse and may one day be used against Australians who download music and TV shows.[23][24]
The Australian people are being sleep walked into a system the attorney general cannot even articulate [...] Right now it would be so easy for me to slip my ex-girlfriend's number in the current process under any investigation [...] No one would pick it up because there is no detail.
On February 22, 2015 Australian Federal Police Assistant Commissioner Tim Morris made the following claims appealing to blind trust from the public.[25]
Your chances that your data will be viewed by law enforcement is low [...] Those with nothing to hide have nothing to fear.
In 2015 the issue of costs became more heavily discussed in the media with figures such as 1% of all national telecommunications revenue annually or "two battleships" per year used.[26]
Prominent parties concerned about the proposals include:[17][24]
- Media, Entertainment and Arts Alliance, the Australian journalists' union
- Timothy Pilgrim, Privacy Commissioner
- Gillian Triggs, Human Rights Commissioner
- the Law Council of Australia
- Communications Alliance
- the Australian Mobile Telecommunications Association
- Fairfax Media
- News Corp Australia
- councils for civil liberties across Australia
- Blueprint for Free Speech
- Australian Lawyers for Human Rights
- the Institute of Public Affairs
- the Australian Privacy Foundation
- Electronic Frontiers Australia
- Privacy International
- George Williams, one of Australia's leading constitutional lawyers and public commentators and University of New South Wales professor
- Dr Keiran Hardy, Research Associate, Faculty of Law, University of New South Wales
Telecommunications and Other Legislation Amendment (Assistance and Access) Act
On 14 August 2018, the federal government published draft text of the Assistance and Access Bill (often referred to by its satirical name, the Ass Access Bill).[27] Modelled after the British Investigatory Powers Act, the legislation was designed to help overcome "the challenges posed by ubiquitous encryption". Under the bill, designated communications providers (which include carriage service providers, any electronic service with end-users in Australia, anyone who develops software likely to be used by a carriage service or an electronic service with end-users in Australia, or anyone who supplies or manufactures components likely to be used in customer equipment likely to be used in Australia") can be ordered to assist in intercepting information relevant to a case, either by means of an existing capability if possible (Technical Assistance Order, TAO), or being ordered to develop, test, add, or remove equipment for a new interception capability (Technical Capability Order, TCO). A "Technical Assistance Request" (TAR) can also be issued, which has fewer restrictions, but is not compulsory.[28][29][30]
Orders must be connected to a warrant under the Telecommunications (Interception and Access) Act or the Surveillance Devices Act. Actions requested under the act must be "reasonable, proportionate, practicable, and technically feasible", and mandatory orders cannot compel a communications provider to add a "systemic weakness or vulnerability, such as requiring one to "implement or build a new decryption capability." or "render systemic methods of authentication or encryption less effective."[31] An annual report must be issued on how many orders and requests are issued. Outside of certain proceedings processes, all specific information on requests and orders are confidential, and it is illegal to publish them publicly.[28][29][30] Only the chief officer of an "interception agency" (which includes the Australian Criminal Intelligence Commission, Australian Federal Police, and state police with permission from the AFP) or the director-general of the Australian Security Intelligence Organisation can issue a TAO or TCO. The Minister for Communications must additionally approve a request for a TCO. A TAR can be issued by these parties, or the Australian Signals Directorate.[28][29][30][32]
The proposed legislation faced numerous criticisms from politicians, advocacy groups, and the tech industry. Liberal Democratic Party Senator David Leyonhjelm argued that the bill was "a draconian measure to grant law enforcement authorities unacceptable surveillance powers that invade Australians' civil rights", alleging that users could be compelled to provide passwords for their personal devices at the request of law enforcement, or be fined.[33][34][35] it was felt that the bill had weaker oversight and safeguards than the equivalent UK legislation, where requests for assistance are subject to judicial review.[29] It was also noted that although providers could not be ordered to do so, they could still be encouraged by the government via a TAR to add a "systemic weakness" to their systems.[30] In testimony, cyptography expert and Stanford Law School attorney Riana Pfefferkorn argued that "whenever you open up a vulnerability in a piece of software or a piece of hardware, it's going to have consequences that are unforeseeable."[36]
The bill was passed by the Parliament of Australia on 6 December 2018 as the Telecommunications and Other Legislation Amendment of 2018, commonly known as TOLA.[36] Bill Shorten of the Australian Labor Party described the bill's passage as being "half a win", since he wanted Parliament to "reach at least a sensible conclusion before the summer on the important matter of national security". He explained that there were "legitimate concerns about the encryption legislation", but that he did not want to "walk away from my job and leave matters in a stand-off and expose Australians to increased risk in terms of national security." Shorten did state that he would consider amendments to the bill when Parliament returned in 2019.[37]
A number of Australian tech firms and startups warned that the bill could harm their ability to do business internationally. Bron Gondwana, CEO of the e-mail host FastMail, felt that the Assistance and Access Bill "makes complying with both Australian law and the EU's GDPR privacy requirements harder, putting Australian businesses at a disadvantage in a global marketplace." After the bill's passing, the service faced concerns and questions over its effects from current and potential users, which has caused a decline in business.[38] Encryption provider Senetas stated that the country could face "the real prospect of sales being lost, exports declining, local companies failing or leaving Australia, jobs in this industry disappearing and related technical skills deteriorating."[39]
In June 2020, as requested by parliament,the Independent National Security Legislation Monitor (INSLM) released a report which recommended changes to the act to require independent and technically competent review of compulsory orders requested under the act.[40]
Specific Incidents
2020 COVID data
The Australian government's Inspector General of Intelligence and Security published a report revealing that Australia's intelligence agencies were caught "incidentally" collecting data from the country's COVIDSafe contact-tracing app during the first six months of its launch from May to November 2020.[2][3]
Raid on journalist's home
On the 4th June 2019, the home of Annika Smethurst, national politics editor of the Sunday Telegraph and other News Corp Australia titles, was raided by the Australian Federal Police.[41] Annika had reported in April 2018 that Australia's Departments of Home Affairs and Defence were discussing a proposal to grant the Australian Signals Directorate (ASD) new powers, such that emails, bank records and text messages of Australians could be accessed by the ASD if the two ministries gave their approval. Currently the ASD is not allowed to spy on Australians, although Australia's domestic spy agency, the Australian Security Intelligence Organisation, can already investigate citizens with a warrant. News Corp Australia called the raid "outrageous and heavy-handed and a dangerous act of intimidation which will chill public interest reporting." The Media, Entertainment and Arts Alliance, a relevant union in Australia, said the police sought to "punish a journalist for reporting a legitimate news story that was clearly in the public interest."[42] It was subsequently reported that Malcolm Turnbull had vetoed the proposal to expand the ASD's powers.[41]
Inquiry in to radio journalist's sources
Also on the 4th June 2019, Ben Fordham, a prominent radio journalist for 2GB, reported that his team had been contacted by an official from the Department of Home Affairs requesting assistance with the investigation in to how he obtained information that up to six boats carrying asylum seekers had recently tried to reach Australia.[42]
Australian Federal Police raid the Australian Broadcasting Corporation
On the 5th June 2019, at least six[43] Australian Federal Police (AFP) officers raided the ABC with a warrant allowing them to access, alter and delete[44] information allegedly in relation to reporting made based on secret files exposing the misconduct of Australian soldiers in Afghanistan. In a statement ABC Managing Director David Anderson said the police raid "raises legitimate concerns over freedom of the press. The ABC stands by its journalists, will protect its sources and continue to report without fear or favour on national security and intelligence issues when there is a clear public interest."[45]
John Lyons, Executive Editor ABC News & ABC Head of Investigative Journalism commented on the raid by the AFP:
I've never seen an assault on the media as savage as this... I've never seen a warrant this comprehensive & I'd say scary... The chilling message is not so much for the journalists, but it's also for the public.[43] I'm still staggered by the power of this warrant. It allows the AFP to "add, copy, delete or alter" material in the ABC's computers. All Australians, please think about that: as of this moment, the AFP has the power to delete material in the ABC's computers. Australia 2019.[44]
The AFP released a statement asserting there was "no link between the execution of search warrants in the ACT suburb of Kingston yesterday (4 June 2019) and those on the Ultimo premises of the ABC today (5 June 2019)."[46]
Travel
International
Australia and the European Union have signed an agreement for the advanced sharing of passenger name records of international travelers. Similar agreements are in place with other countries.
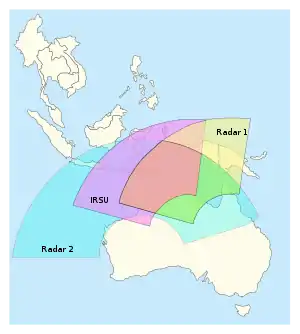
In addition to passenger information and standard radar, Australia uses the Jindalee Operational Radar Network to detect individual boats and planes in the north and west of the country.
It not only provides a 24-hour military surveillance of the northern and western approaches to Australia, but also serves a civilian purpose in assisting in detecting illegal entry, smuggling and unlicensed fishing. The system also assists in weather forecasting making it possible to produce wind and sea state maps from information provided by the network. These maps can give early warnings of cyclones and enable ships to save fuel by avoiding rough weather.
— Jindalee Operational Radar Network, DSTO website
Domestic
Vehicles can be tracked by a range of systems including automatic number plate recognition (ANPR), video and sensor-based traffic surveillance networks, cellular telephone tracking (if a device is known to be in the vehicle) and automated toll networks. The ANPR systems are intelligent transportation systems which can identify vehicles and drivers. ANPR is known under various names in Australia: SCATS in Sydney, New South Wales; ACTS in Adelaide, CATSS in Canberra, SCRAM in Melbourne, DARTS in the Northern Territory and PCATS in Perth.
New South Wales
In December 2014, certain universities such as Sydney University delayed collaboration with the new Opal card system scheduled to fully replace existing, anonymous paper tickets on New South Wales mass transit, citing privacy concerns,[47] whereas Macquarie University, University of New South Wales and Australian Catholic University had already agreed to provide the "student data" to the card network. Data is made available to other NSW government departments and law enforcement agencies.[48] Concerns about privacy have been repeatedly raised in the mainstream media, with commentators questioning the extent to which user data can be accessed by authorities.[49][50][51] According to the Opal Privacy Policy, data is made available to other NSW government departments and law enforcement agencies.[48] On the 13th of March 2015 it was announced that Opal cards would be linked to commuter car park spaces, such that private road vehicle identities would become associated with individual mass transit use.[52]
Other states
The extent and frequency to which individual traveler data is released without a warrant remains poorly documented for the following systems:
- go card, Brisbane's smartcard system
- Metrocard, Adelaide's smartcard system
- myki, Melbourne's smartcard system
- SmartRider, Perth's smartcard system
Related law
 |
|---|
| This article is part of a series on the politics and government of Australia |
| Constitution |
This section outlines the main legal references for mass surveillance in Australia.
National
Under Australian law, the following acts are prominent federal law in the area of surveillance.
- Telecommunications (Interception and Access) Act 1979 (formerly known as the Telecommunications (Interception) Act 1979)
- Telecommunications Act 1997
- Surveillance Devices Act 2004
- Privacy Act 1988
- Intelligence Services Act 2001
- Intelligence Services Amendment Act 2004
A separate body of state-level laws also exists.
International agreements
Australia is part of the Five Eyes international surveillance network, run by the United States National Security Agency and generally protected from public scrutiny citing 'national security' concerns. According to the Canberra Times and cited policymakers, one of the most prominent critics of these agreements was the Australian National University academic Des Ball, who died in October 2016.[53]
See also
- Parliamentary Joint Committee on Intelligence and Security
- Mass surveillance industry
- Defence Science and Technology Organisation, particularly the Wide Area Surveillance Branch of the Intelligence, Surveillance and Reconnaissance Division (ISRD) with respect to Jindalee Operational Radar Network
- Five Eyes
- Internet censorship in Australia and Censorship in Australia
- Passenger name record
- Pine Gap, Shoal Bay Receiving Station, HMAS Harman and Australian Defence Satellite Communications Station
- Telephone recording laws#Australia
References
- "Surveillance of the Financial System". Reserve Bank of Australia. 1999.
- "IGIS Report toOAIC on COVID app data - 16 May to 16 November 2020". Inspector General of Intelligence and Security. November 2020.
- Zack Whittaker (24 November 2020). TechCrunch https://techcrunch.com/2020/11/24/australia-spy-agencies-covid-19-app-data/. Missing or empty
|title=(help) - "Law enforcement (Telecommunications): Identity verification in relation to pre-paid mobile services". Australian Communications and Media Authority.
- "Telecomms & law enforcement: obligations". Australian Communications and Media Authority.
- "Aus becoming surveillance state: Ludlam". ZDNet. 20 January 2012.
- Nick O'Malley and Ben Grubb (7 June 2013). "Australians at risk in US electronic surveillance program". Sydney Morning Herald.
- "Google Transparency Report: Australia".
- Peter Micek and Matt Solomon (16 April 2014). "Australian Telco Telstra Releases First Transparency Report".
- "Telstra Transparency Report: 1 July - 31 December 2013" (PDF).
- "More than 500 authors sign global petition to protest mass surveillance". The Australian. 10 December 2013.
- Dorling, Philip (8 July 2013). "Snowden Reveals Australia's Links to US Spy Web". The Sydney Morning Herald. Retrieved 2 August 2013.
- Ben Grubb (20 August 2014). "Telstra found divulging web browsing histories to law-enforcement agencies without a warrant". Sydney Morning Herald.
- Aaron Gluck Thaler (15 August 2014). "Australia government pushing to expand surveillance, hacking powers". Privacy International.
- Ben Grubb (26 February 2015). "What George Brandis and Malcolm Turnbull can do to fix metadata muddle". Retrieved 26 February 2015.
- Gillian Lord (25 July 2014). "Privacy fears as Australian surveillance laws are dragged into the digital era". The Guardian.
- Ben Grubb (12 March 2015). "Dutch do a U-turn on metadata laws". Sydney Morning Herald. Retrieved 13 March 2015.
- "Here's How Much Access Australian Police Already Have to Your Data". Sydney Morning Herald. 11 September 2017.
- "TELECOMMUNICATIONS (INTERCEPTION AND ACCESS) ACT 1979: Annual Report 2015–16" (PDF). Attorney-General's Department.
- "Citizens Not Suspects: Learn More".
- James Massola and Ben Grubb (9 August 2014). "Data retention Hokey Pokey: Liberals caught in public embarrassment over privacy".
- Ben Grubb (22 August 2014). "Metadata ambiguity to be resolved by government data retention policy paper: sources". Sydney Morning Herald.
- Marc Fennel (19 February 2015). "Metadata regime open to abuse: insider". Download This Show. Australian Broadcasting Corporation.
- Ben Grubb (21 February 2015). "Trust spies and police on metadata retention to fight terrorism and crime, Attorney-General George Brandis pleads". Sydney Morning Herald. Retrieved 23 February 2015.
- Lia Timson (22 February 2015). "Metadata retention: 'Those with nothing to hide have nothing to fear', says Australian Federal Police Assistant Commissioner Tim Morris". Sydney Morning Herald.
- Ben Grubb (2 March 2015). "Australians harass George Brandis as the true cost of metadata retention is revealed". Retrieved 3 March 2015.
- Australian Cyber Assistance & Access Legislation, The ASS Access Bill 2018 Highpants 20 September 2018
- Stilgherrian. "Australia's anti-encryption law will merely relocate the backdoors: Expert". ZDNet. Retrieved 26 April 2019.
- Bogle, Ariel (2 October 2018). "Australia's surveillance laws could damage internet security globally, critics say". ABC News. Retrieved 26 April 2019.
- Stilgherrian. "What's actually in Australia's encryption laws? Everything you need to know". ZDNet. Retrieved 26 April 2019.
- Stilgherrian. "No backdoors for Australian encryption, just a riddling of ratholes". ZDNet. Retrieved 26 April 2019.
- Mann, Monique. "The devil is in the detail of government bill to enable access to communications data". The Conversation. Retrieved 26 April 2019.
- "Industry associations pressure Government against "rushed" decision on Assistance and Access Bill". ARN. Retrieved 26 April 2019.
- Kruger, Colin (1 October 2018). "'Five Eyes' and tech giants closely watch Australia's spyware bill". The Sydney Morning Herald. Retrieved 26 April 2019.
- "Apple Sounds Alarm over Australia's Proposed Anti-Encryption Law".
- "Australia passes new law to thwart strong encryption". Ars Technica.
- Hunter, Fergus (7 December 2018). "Bill Shorten says Labor achieved 'half a win' on encryption legislation". The Sydney Morning Herald. Retrieved 26 April 2019.
- "FastMail loses customers, faces calls to move over anti-encryption laws". iTnews. Retrieved 25 February 2019.
- Koehn, Emma (7 December 2018). "'1984' style encryption laws will stymie startup growth: founders". The Sydney Morning Herald. Retrieved 26 April 2019.
- Catania, Corrs Chambers Westgarth-Philip; Rozario, Michael do; Magness, Phillip. "Australia's security monitor recommends changes to controversial 'anti-encryption' legislation | Lexology". www.lexology.com. Retrieved 27 July 2020.
- "Malcolm Turnbull canned any idea of allowing the ASD to spy on Australians".
- "Australian journalist's home raided over spying report". BBC. 4 June 2019.
- "John Lyons Video Interview with ABC". ABC.
- "John Lyons tweet". ABC Editor.
- "ABC raid: Outcry as Australian police search public broadcaster".
- "AFP statement on activity in Canberra and Sydney". Australian Federal Police. 5 June 2019.
- Pallavi Singhal. "Student Opal card privacy concerns limit university participation".
- "Opal Privacy Policy" (PDF). Archived from the original (PDF) on 6 March 2014.
- Riemer, Kai. "Privacy has taken a back seat amid the Opal debate". Sydney Morning Herald. Retrieved 9 June 2014.
- "Sydney Opal card travel history can be accessed by police". 30 June 2014.
- "No warrants needed to access Opal card records". Sydney Morning Herald. 15 July 2014.
- Jacob Saulwick (13 March 2015). "Opal access? New car parks for Western Sydney stations could be restricted to rail commuters". Sydney Morning Herald. Retrieved 14 March 2015.
- Daniel Flitton. "Des Ball: a rare influence on thinking about secrets and war".
External links
- OpenAustralia Search: Parliamentary records mentioning 'surveillance'.